Home » Curtin (Page 3)
Category Archives: Curtin
Digital Culture Links: September 21st 2011
Links for September 7th 2011 through September 21st 2011:
- Game over for Japanese teens as grey gamblers take prime slot at arcades [News.com.au] – “The country which gave the world classic arcade games such as “Space Invaders” and “PacMan” is facing a demographic crisis, with a dwindling birth rate and ever-swelling numbers of elderly people. So Japan’s amusement arcades, once an exclusive resort of youth, are increasingly becoming the abode of the old, The (London) Times said today. According to the Hello Taito game centre in the Tokyo suburb of Kameari, as many as 90 per cent of its weekday visitors are over 60 years old. In an effort to encourage elderly customers, the company is making concerted efforts to appeal to this unfamiliar demographic. Metal stools have been replaced by benches covered with old-fashioned tatami mats. Seaweed tea, popular among retired people, is provided free, as well as blankets and reading glasses. Even the deafening noises emitted by the arcade machines have been turned down to a minimum out of consideration for geriatric sensibilities.”
- Ctrl-Z new media philosophy – New broadly-themed and inclusive academic journal looking for submissions under the broad umbrella of “New Media Philosophy”.
- Harried, underpaid staff plan to flee the sector [The Australian] – *sigh* “Two in five academics under the age of 30 plan to leave Australian higher education within the next five to 10 years because of high levels of dissatisfaction caused by lack of job security, poor pay and mountains of paperwork and red tape. And for those aged between 30 and 40, the figure is one in three. Dissatisfaction and insecurity are so rife among casual and sessional staff that a new report for the Department of Education, Employment and Workplace Relations estimates that close to half the academic workforce will retire, move to an overseas university or leave higher education altogether within the next decade.”
- Online gamers crack AIDS enzyme puzzle [The Age] – Collaborative online gamers manage to crack a crucial enzyme which is key to combating HIV. This is tangible evidence of collective intelligence of game players when usefully directed and harnessed.
- danah boyd | apophenia » Guilt Through Algorithmic Association – How algorithms can make someone look guilty or attached to something, even if it’s only other searchers making that connection: “You’re a 16-year-old Muslim kid in America. Say your name is Mohammad Abdullah. Your schoolmates are convinced that you’re a terrorist. They keep typing in Google queries likes “is Mohammad Abdullah a terrorist?” and “Mohammad Abdullah al Qaeda.” Google’s search engine learns. All of a sudden, auto-complete starts suggesting terms like “Al Qaeda” as the next term in relation to your name. You know that colleges are looking up your name and you’re afraid of the impression that they might get based on that auto-complete. You are already getting hostile comments in your hometown, a decidedly anti-Muslim environment. You know that you have nothing to do with Al Qaeda, but Google gives the impression that you do. And people are drawing that conclusion. You write to Google but nothing comes of it. What do you do? This is guilt through algorithmic association.”
- Marilyn Monroe, Grace Kelly and Marlene Dietrich join Charlize Theron in new Dior J’Adore advert [Mail Online] – Marilyn Monroe, Grace Kelly and Marlene Dietrich all posthumously join Charlize Theron in a new perfume advertisement thanks to the plasticity of computer generated imagery.
Creepy: Educational Tool or Privacy Nightmare?
Like Please Rob Me and I Can Stalk U before it, Creepy is an application which lives up to its name. It’s a recently-released basic desktop application (Windows or Linux) which scrapes Twitter and a bunch of image sharing services, including Flickr, TwitPic and yFrog, and builds a diary and map of someone’s movements and the times these were logged. Now, Creepy only accesses data which is public, data which is shared online but, like Please Rob Me or I Can Stalk U, it presents this data is a way which isn’t conventionally available. More to the point, when confronted with a map of your day-to-day activity, plotted on the basis of social media activity, it can be quite confronting. The tool is described thus on the website:
creepy is an application that allows you to gather geolocation related information about users from social networking platforms and image hosting services. The information is presented in a map inside the application where all the retrieved data is shown accompanied with relevant information (i.e. what was posted from that specific location) to provide context to the presentation.
Additionally, the FAQ adds this detail and rationale:
1) Dude, this app is disturbing , what were you thinking ?
Well, I don’t think that the fact that your geolocation information can be gathered and aggregated is disturbing. The fact that you were publishing it in the first place , is , on the other hand. Just to be clear, the intention behind creating creepy was not to help stalkers or promote/endorse stalking. It was to show exactly how easy it is to aggregate geolocation information and make you think twice next time you opt-in for geolocation features in twitter, or hitting “allow” in the “this application wants to use your current location” dialog on your iphone.
So Creepy does explicitly claim to be an educational tool in the ‘here, look what you’ve already done, now change your habits’ kind of way. Running Creepy just based on my own Twitter information produced a rudimentary map of my logged activity in Perth (clearly Creepy is following data from FourSquare and Flickr images which I posted with my Twitter account):
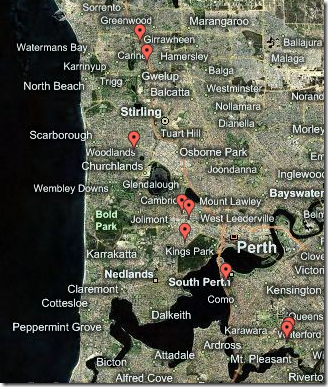
However, when I zoom in a long way, for example onto my workplace, there’s certainly a quite explicit level of geographic information:

Now, I’m well aware of the data trail my Twitter, FourSquare and Flickr photos generate and acknowledge that if someone wanted to they could aggregate that information and build a reasonable picture of my activity. The point, though, is that many people aren’t that aware of the data trails they are leaving and that’s what Creepy purports to fix: it’s a very visible, confronting and explicit visualized map of the data trail you’re leaving. It’s not a technical privacy violation, but it might feel like an invasion of sorts. If it does feel that way, perhaps it’s time to think a little more about how, when and where you share information about yourself on social media and what data is actually embedded in your photos.
Reputation Management and Social Media
Today the Pew Research Centre’s Internet and American Life Project released their report Reputation Management and Social Media (2010) which is based on research undertaken late 2009. There is a great deal of important and topical information in the survey, with the US results likely to be slightly higher but certainly comparable to trends in Australia. I want to really draw attention to the way that younger adults are using social media according to this report, using three of Pew’s graphs to talk about their findings.
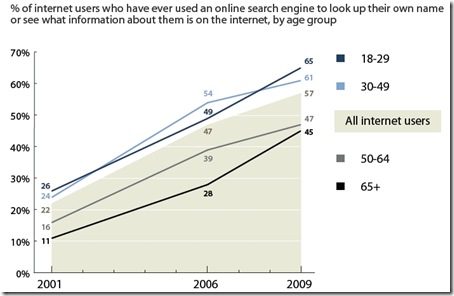
The first graph indicates how many internet users search for their own name online:
This result is particularly interesting for two reasons: firstly, it shows that across the board, interest in our own web presences has increased dramatically across the last decade; and secondly, it highlights that younger adults (those 18-29) appear to be the most concerned with their online reputation. As danah boyd celebrated earlier today, this result really undermines the cultural myth that younger people are the least interested with online privacy. Obviously this survey excludes people under-18, but it’s fair to assume that part of the process of growing up these days includes becoming sensitised to the importance of being aware of our web presence.
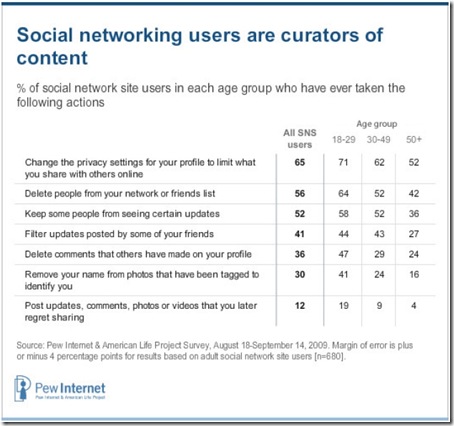
Similarly, the Pew report also highlights the face that younger people are the most active in controlling their presence online, insomuch as they are most likely to have changed their privacy settings on social networks, they are the most likely to untag a photo of themselves, and so forth:
Here we see that younger people are also the most conscious of shaping their web presence, by editing who can see what they share online, and which elements of the digital artefacts linked to them remain visible, and remain linked to their names.
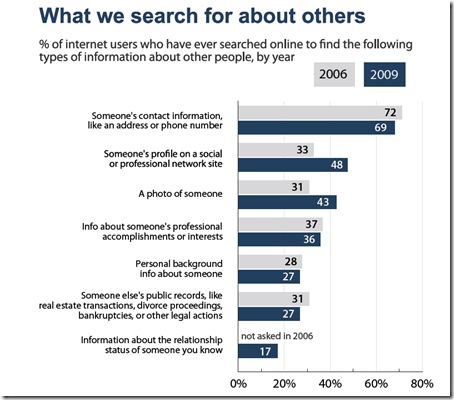
The last Pew graph shows how much information people are seeking about others online:
Everything from contact details to photos are being sought online, which similarly highlights how important it is that everyone be aware of what their web presence really ‘says’ about them.
Since I teach in the Internet Studies department here at Curtin, it’s hardly a surprise that all of this information is vital to consider when we design the learning experiences our students encounter. In the first-year unit Web Communications 101, the notion of web presence is our central organising theme. However, one of the distinctions we make, which Pew does not, is the difference between digital traces we leave purposefully, and maintain control over, versus those we don’t. In Web Comms 101, as Pew does, we talk about footprints, but we also talk about digital shadows, those bits of digital media that are somehow attached to our names, or chosen identities, which we have minimal, if any, control over. Given how much people search for each other, and how much thought is going into how we appear online for the average internet user, it’s probably how we address and deal with those shadows which will be one of the most important topics to seriously consider in the coming years.
Developing a Web Presence During Candidature
I gave a short seminar today on the topic of developing a web presence during candidature. Honours, masters and doctoral students increasingly need to be aware of the tools and conventions that most directly allow them to be part of their scholarly field online. Hopefully this presentation gave some students here at Curtin some beginning ideas. I fear the slides are somewhat less useful without the presenter, but on the off chance they’re useful to anyone, here you go:
As always, comments are most welcome.
Learning, Authenticity & Online Policy Primers
This year I’ve been enjoying designing and implementing a series of new assignments and assessment techniques with students in our Internet Studies programmes. One of the most challenging things about working in Internet Studies is trying to make assignments authentic – which basically means doing assignments which can end up being meaningful and, ideally, viewable by the world-at-large on the Internet. One assignment that has worked particularly well and I thought worth sharing is from the unit Online Politics and Power, which looks at power in various guises and instances online.
One of the most interesting ways power is deployed online is through those infamous Terms of Use and Terms of Service which 95% of people never read, but always agree to, when signing up for a new service. So, I thought it’d be useful to ask students to really interrogate the Terms of Service of some online tools and platforms. More to the point, I wanted this to be a useful assignment beyond the confines of a university unit. So, I asked students to find a way to communicate the core elements of some Terms of Use in a way that would be accessible to the general public, hence an Online Policy Primer. (If you’re interested the assignment outline and requirements are online here.)
I have to say, I was blown away by how good the Primers are, and how, ultimately, useful they are, too. Also, while we did discuss the Creative Commons, I didn’t stipulate that students had to use a CC license, but I was delighted that many chose to do so. Of those that did, I’d like to share three stand-out examples.
The first, by Paula (@MXYZ_), takes a close look at Flickr’s Terms of Service and is licensed under a Creative Commons Attributions Share-Alike license [CC BY SA]:
The second, by Simon (@whoisimon) explores the Terms of Service for Slideshare and is licensed under a Creative Commons Attribution, Non-Commercial, Share-Alike license [CC BY NC SA]:
And the third, and final, policy primer I wanted to highlight is by Chea Hwey Yea, looking at Twitter’s Terms of Service and is also licensed under a Creative Commons Attribution, Non-Commercial, Share-Alike license [CC BY NC SA]:
These are just three examples of the many, many wonderful primers students created; while not everyone used a Creative Commons license, three more Primer’s worth highlighting are a machinima presentation exploring Second Life’s Terms of Service created by Rhys Moult, Renee Bird’s close look at the Terms of Use for the Multiplayer Online Game Evony, and Veronica Fry’s analysis of YouTube’s Terms of Service.
As you can see, these students have a lot to be proud of and have, in many cases, created Primers which are likely to be useful well beyond the confines of the unit!
Privacy, Power, Permanence & Politics!
One of the reasons I’ve been so quiet is that in the past few weeks I’ve started teaching two new units here at Curtin. Both of these units have been completely redeveloped and this is their first run in the new form. I’ll talk about Web Communications 101 another day, but I wanted to point out how much I’m enjoying teaching our new Internet Politics and Power unit. The unit has a healthy dose of thinking from people like Lessig and Zittrain and really tackles many of the big issues for digital culture today. So I’m now required to stay on top of many of those issues I like to blog about, like privacy and copyright, rather than having to steal a hour here or there! 🙂 There are so many issues that are relevant today, but one area which is really getting me thinking is the way that Apple, Google, Facebook and others are creating their own bounded realms of control!
A recent example that really highlights the complexity of these issues is the policing of Apple’s application store for the iPhone. Recently there was a a fairly heated discussion after Apple rejected the Ninjawords: iPhone Dictionary application ostensibly for offensive words (but words which are present in many other apps). It turns out Apple had more complex reasoning which was, among other things, wrapped up with new parental controls being introduced for apps. While this rationale is less bizzare, John Gruber still makes the very important point that the biggest issue is there needs to be "fairness, consistency, and common sense in the App Store review process" and that consistency is, thus far, sorely lacking.
Apple’s app store has also been under fire for rejecting a Google app which would allow many users to access cheaper calls and services. Elisabeth Oppenheimer, writing at Zittrain’s Future of the Internet blog, notes that Apple claimed that they rejected Google’s app since it "duplicates iPhone functionality" but in real terms many people suspect it was rejected since it threatened the monopoly AT&T have enjoyed in being the exclusive iPhone service provider in the US. Oppenheimer is "hopeful that killing Google Voice will be the one step too far that inspires consumers and regulators to sit up and work to get sensible open-access rules" but I’m not necessarily that optimistic.
Meanwhile, Rupert Murdoch is demanding Amazon hand over the details of Kindle users who subscribe to media from Murdoch’s vast empire. So far Amazon has not complied, but I wonder if they’re willing to risk their relationship with Newscorp in the long run? Along similar lines, this week Facebook purchased Friendfeed which potentially adds even more information to Facebook’s vast array of user information that they manage in, at times, curiously questionable ways.
While not quite an app, on another front the permanence of archives has come under threat from another third-party tool. While there have been concerns for a while about URL-shortening services, the upcoming closure of tr.im is the first one that I know of to go under. These services have become extremely popular, allowing people to create tiny web page addresses that can fit alongside a tweet and still fit Twitter’s 140 character limit. However, what will happen to all of the tweets which contain tr.im address? They’ll go dead, effectively making those tweets useless. While tr.im is not really to blame (really, what is the business model for a URL-shortener?), our reliance on these services leaves our tweets and related links fragile and vulnerable when a company or service collapses under the weight of their own popularity. This is less a privacy issue than an issue of utility: relying on third-party tools with no real backup function leaves the usefulness of our personal and collective archives in the hands of folks who, ultimately, may not have the resources to run these services forever!
Update: On the tr.im font there appears to be a happy ending, with the announcement that tr.im is becoming a community-developed open source project.
Update 2: Apple claim that they “did not reject an iPhone application submitted by Google and that it was still studying it, in part because of privacy concerns.”